WannaCry Detection Using Zenmap?
The WannaCrypt0r (a.k.a WannaCry, WCry) Ransomware making rounds worldwide, has become one of the greatest threat to Cybersecurity.
This ransomware affects the confidentiality, integrity and availability of information as it leverages on social engineering or spam emails, tricking users into downloading and executing infected attachments. This attachment when clicked installs the WannaCry worm on the targeted system, encrypting every single file on it and replicating itself across the network. It doesn’t get better as this worm propagates itself on the network and infects all vulnerable computers using the Windows Server Message Block (SMB) Protocol Version 1, even if the computers are not connected to the internet for the encryption process to take place. Ransomware is deadly.
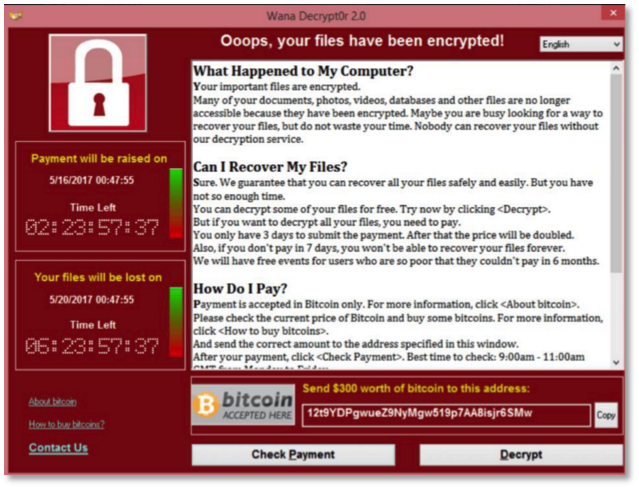
We took a look at the bitcoin addresses hard coded in the WannaCry Ransomware and people are paying big time. At the time of writing, the WannaCry attackers have received over 42.91 BTC. Check out the BTC addresses here;
https://blockchain.info/…/115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
https://blockchain.info/…/12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
https://blockchain.info/…/1HgcjDJEwe6KBTnEoXURL6UNscdpw9Vehm
One has 12.68 BTC the second has 16.86 BTC and the third has 13.37 BTC for a total of almost $82,977.
Mitigation Strategy
There is currently no WannaCry decryption tool, however, you can use this open source tool “Zenmap” to find out if a system(s) is vulnerable to MS17-010 (ETERNALBLUE) which the WannaCry ransomware leverages on.
Zenmap is an official Nmap Security Scanner GUI. It is a multi-platform (Linux, Windows, Mac OS X, BSD, etc.) free and open source application. Please follow these steps;
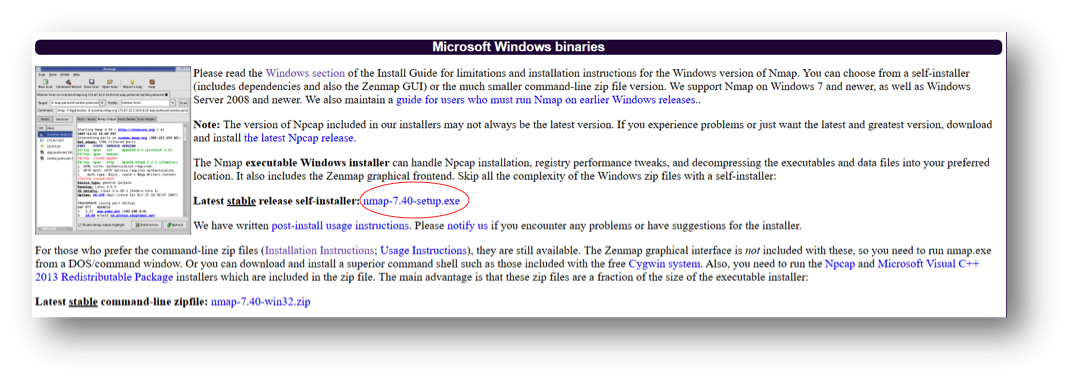
STEP 1
Goto to https://nmap.org/download.html to download and install ZENMAP.
STEP 2
Download the smb-vuln-ms17-010.nse file and Paste in C:\Program Files (x86)\Nmap\scripts
STEP 3
- Launch the Zenmap application,
- Type; nmap -p445 –script smb-vuln-ms17-010 <insert ip address>
- Click Scan as shown below.
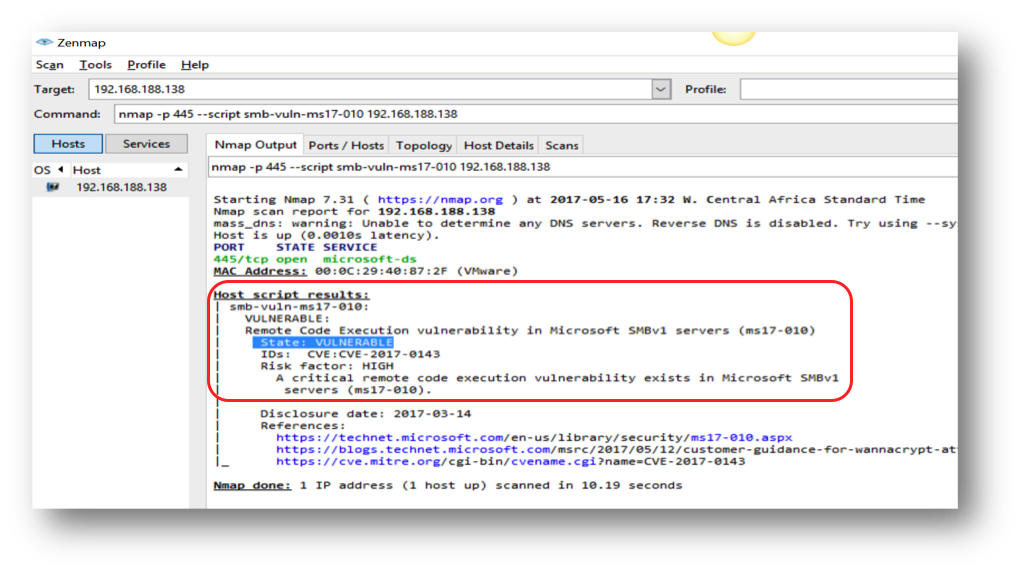
STEP 4
If the system is vulnerable to Eternalblue, the scan result will show as below.
STEP 5
Download and install the emergency patch https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/.
Microsoft released patches on May 12, 2017 for end of life (EOL) versions Windows, such as Windows XP, Windows 8, Windows Server 2003, and Windows Server 2008.
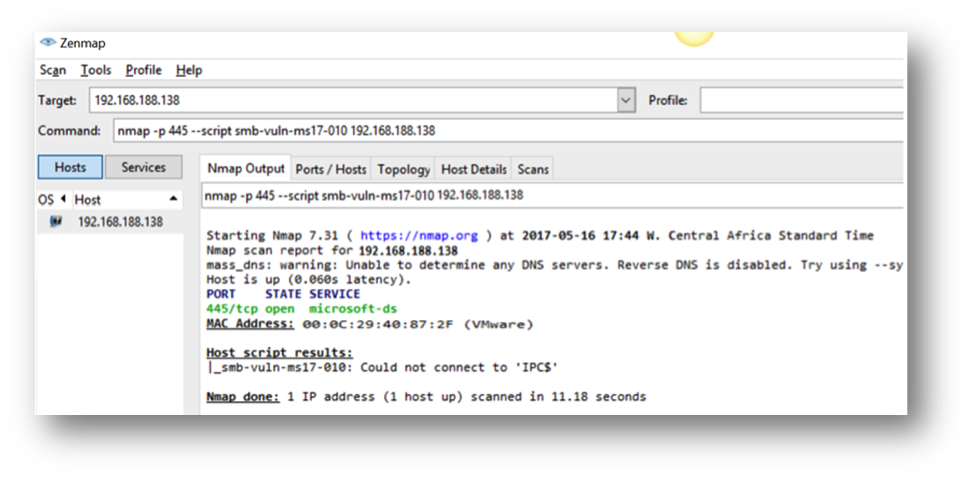
STEP 6
Rescan to confirm it is no longer vulnerable as shown below
Other Precautions to be taken;
- Be extremely suspicious of all emails particularly those containing attachments or web links which you might be asked to open.
- Users should watch out for unsolicited emails. If you are not sure of the source of an email, DO NOT OPEN links or any attachments in it. Simply delete such emails.
- Regularly backup critical files offline.
NB: The ransom demands $300 -$600. We cannot confirm whether files will be released after payment. The best strategy for now is to prevent this attack which cuts across all Microsoft Windows workstations (excluding Windows10), servers and ATMs. Hence, all Windows operating systems need to be patched immediately.


Leave a Reply